Quantum Optics Seminar by Pepijn W. H. Pinkse
Quantum-Secure Authentication and Adaptive Quantum Optics
Modern society strongly relies on secret information for authentication. However, keeping information secret and accessible is exceedingly difficult in modern society. We experimentally demonstrate Quantum-Secure Authentication (QSA) that does not require keeping secret information but relies on an optical Physical Unclonable Function (PUF) as a key [1]. As illustrated in the figure, we illuminate the key using light containing fewer photons than spatial degrees of freedom. In the key the photons are multiple-scattered by millions of randomly organized nanoparticles. The spatial shape of the returned (“response”) photons depends strongly on the positions of the scatterers and on the incident (“challenge”) photons. Assuming its challenge-response behavior is known, the key can be authenticated by illuminating it with a challenge and verifying whether the response is as expected. Because of the low photon number, an attacker cannot fully characterize the challenge. Therefore, he cannot digitally construct the correct response even if the challenge-response behavior of the key is publicly known. QSA is secure if the physical key is too complex to be copied with current technology, as is believed to be the case for e.g. white paint.
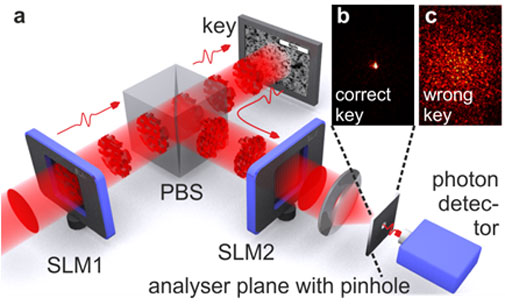
Fig 1. a, Quantum-Secure Authentication setup. A spatial light modulator (SLM1) transforms a weak laser beam into a “challenge” that contains more spatial degrees of freedom than photons. The optical multiple-scattering key converts the challenge into a “response”. SLM2 is programmed to convert the expected response into a plane wave. b, If the key is correct, the few-photon response will be focused onto the detector. c, If the key is wrong, the few-photon response will not be focused onto the detector. Image from [2].
QSA is an intriguing application of “Adaptive Quantum Optics”, the combination of quantum optics and adaptive optical methods counteracting or even exploiting disorder. In a recent work [2] we demonstrate that with wavefront modulators, multiple-scattering materials can be turned into programmable linear optical networks. In such a network, resembling an asymmetric lossy beamsplitter [3], we demonstrate programmable two-photon quantum interference.
